Trojan Horse Virus Icon Outline Style

Trojan Horse Removal Protecting Troy Emsisoft Security Blog

Regin Spying Software Has Been Attacking Governments And

Trojan Horse Images Stock Photos Vectors Shutterstock
Trojan Horse Malware Computer Icons Computer Security

What Is A Malware Virus V S Trojan What S The Difference
The Best Free Trojan Drawing Images Download From 152 Free
Trojan Horse Drawing At Getdrawings Com Free For Personal

Trojan War Cartoons And Comics Funny Pictures From

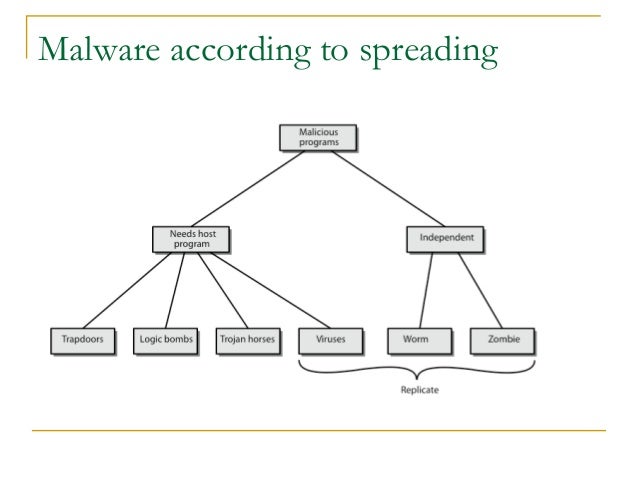
The Difference Between A Virus Worm And Trojan Horse Symantec

Icon Computer Virus Black Trojan Horse Computer Virus

Viruses Worms And Spyware Yikes A Look At Malware
Trojan Horse

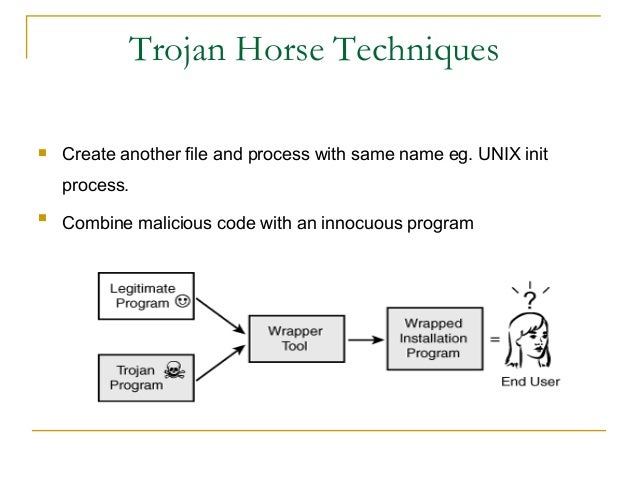
Trojan Horse Computer Virus Computer Worm Malware Firewall

Trojan War Cartoons And Comics Funny Pictures From

What Is Malware Everything You Need To Know About Viruses

Animation How New Trojan Horse Antibody Strategy Kills Ebola

World S Best Trojan Horse Stock Illustrations Getty Images

Free Art Print Of Trojan Horse Dragged

Trojan Horse Trojan War Computer Virus Gifts Png Clipart
Trojan Horse

Trojan Horse Virus Computer Destroy Laptop

Trojan Horse With Worm Inside Computer Virus Symbol Grunge

Trojan Horse With Worm Inside Computer Virus Symbol Grunge

Bonus Material Trojan Horse Play Creative Control

Trojan Horse Computer Virus Artwork Drawing U25439863

Gray Laptop And Blue Snake Illustration Computer Worm

Common Malware Types Vulnerability Management 101 Veracode

Trojan Horse

Trojan Horse Malware Computer Virus On Computer Stock

Trojan Horse Blueprint Stock Illustration Download Image

Smartphones Social Media And The Trojan War The Daily Star

Horse Trojan Horse Trojan War Computer Computer Virus

Kfor Basic Information
Computer Trojan Horse Icon Outline Computer Trojan Horse

8 Different Types Of Malware United States Cybersecurity

Trojan Horse With Worm Inside Computer Virus

What Is Malware Everything You Need To Know About Viruses

Vector Art Virus Attack On Internet Browser Clipart

Computer Virus Trojan Horse Malware Computer Security Skull

12 Arrests In Europe For Trojan Horse Cybercrime
No comments:
Post a Comment